As data operations have expanded and grown more complex, risk of disasters and outages has increased and this can cause significant downtime to your company’s operations, often resulting in a large potential loss of revenue. However, downtime is not the only potential consequence of security breaches. CPM/EPM software have been developed to meet the needs of finance but beyond that have also been structured to address many concerns and vulnerabilities as they relate to data integrity. Before we explore how EPM addresses these concerns, lets discuss the types of risks:
- Financial Information Leak: Perhaps one of the most critical types of leaks, a company’s financial information making its way into the hands of a hacker can cause the most direct form of loss by exposing charge card numbers/expiry dates, bank account information, confidential reports, or investment details.
- Business/Operational Plans: The information that a company documents for regular business processes such as intellectual property resources and research data can be vital to the company’s future success in any given market. This can include product maps, marketing initiatives, pricing plans, patents, manuals, and much more. It is important to have this data protected and confidential to avoid information leakage to competitors, customers, and other players in the market.
- IT Security Breach: There are likely several different information systems that a company uses to handle all aspects of the business, and companies have a unique structure or strategy to leverage the information systems. A breach of IT Security can lead to vulnerabilities of usernames/passwords, encryption keys, network structure, or VPN information.
- Personal Information Leak: The applications hosted on a server can sometimes contain very specific personal information of employees or customers such as social security numbers, personal contact info, education, health related info, birthdates, etc... Information of this nature falling into the wrong hands presents many risks, including but not limited to, identity theft, fraud, and even personal danger.
Let us now discuss some ways to avoid these negative repercussions of data security breaches.

Data integrity
is an important and evolving concept, and below I have posted some of the keys for organizations to look out for when trying to create an effective and secure data structure/strategy. These data integrity standards have been published by the FDA and are known by the ALCOA acronym:
Attributable
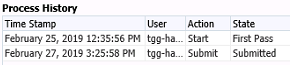
Changes in data need to be attributable to a specific user. It is important to know who has made edits so that any errors or questions can be traced back to the person who originally inputted or edited data. EPM tools allow administrators to track user activity as shown below.
Legible
All data is recorded for a purpose, and the way the data is displayed needs to make sense with regards to its purpose. This does not mean that everyone should be able to look at a set of data and understand exactly what it means, as some data sets are complex and only make sense if you understand the underlying structure. At the same time however, the data needs to be legible and useful to the users.
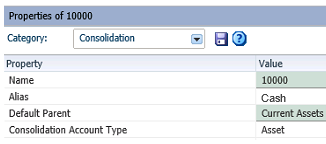
EPM software has built in functions to help users and administrators get on the same page with regards to the structure and use of the data. The different types of metadata have a lot of descriptive properties and intuitive functionalities to make the data understandable and meaningful. The below screenshot shows an example of some properties used to describe a “cash” balance sheet account.
Contemporaneous – Data should be recorded as it was observed, and at the time executed. This means that information about when the data was accessed, added, changed, or observed should be recorded.
EPM tools make data contemporaneous usually through a process history function, which was displayed on the screenshot in the “Attributable” section above. Note that it shows which user updated the status of a review, and the exact time to the second that the status was changed
Original
Source data should be available in its original form. The original source data however should not be easily editable. For example, providing users with read only access is a good solution for maintaining the accuracy of original source data.
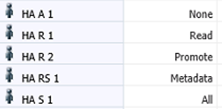
This concept is often practiced in EPM by creating copies of the app to make changes on and keeping original source data in a dev environment with restricted access and only moving out a copy into prod for users to manipulate and write over. Below is an example of how an EPM administrator can provision access rights to users to put restrictions on specified data:
Accurate
Meaning that the data should not contain any errors in the numbers or in the logic itself
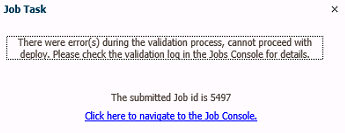
EPM tools help users get the correct logic by running validation tests and making data EPM data comparable with original ledger data to ensure everything is the same. When we find discrepancies between the source data (ledger) and the EPM data, we can use audit trail functions to go back and see where the miscalculation happened and correct it. EPM tools often have relevant logic programmed into them, and they will stop you from going further with an operation if it does not follow the correct logic. An example is shown below:
Now we have looked at several different ways that poor data security can threaten a business, and we’ve also looked at some key principles to follow to strengthen your organization’s data integrity. As companies are striving for survival and success in an era where digital transformation is moving faster than security and privacy regulations, precise proactive security measures need to be taken to avoid disruptions to IT systems. We’ve outlined some examples of how EPM software can assist with data integrity principles, but the effort doesn’t stop there. In the pursuit of continued long-term success, companies need to constantly stay up to date with security trends and continue to promote secure infrastructures for information systems.

